IT & Cloud Solution Skillsets of Axis Tech
Technology Skill Sets
We are providing futuristic services

Data Centre Build and Consulting Services
Data Centre Build and Consulting Services
A primary concern for IT management is choosing how to correctly size the overall data center infrastructure. Data Centre Solutions is committed to excellence in the data center design/build process. Our proven methodology is designed to minimize the disruption of your business during deployment. These are just some of the services we offer…
Data Centre Build and Consulting Services
Asset Management
- Extensive detail and asset information including servers, networking, and storage
- Instantly get a picture of what assets you have, who owns them and where they are located
- Reports facilitate auditing and compliance of your assets
- Quickly search for assets and get detailed information with a click
Capacity Management
- Available power outlets on rack PDU
- Available power capacity at rack and upstream
- Available network ports with media & connector match
Change Management
- Issue Request, Approve Request
- Issue Work order, Complete Work order
- Monitor and Manage
- Remove unnecessary steps and delay from manual efforts
- Verify all information is within request and all parties are informed
- Coordinate and eliminate duplicate requests.
Energy Management
- Automatically collect data from Building feeds, IT loads, and non-IT loads
- Automatically calculate and trend PUE in all data centers across the world
- Immediately see the impact of energy efficiency initiatives
- Compare your PUE Year over Year and with industry peers
Environment Management
- Interactive Data Center Health Map
- Real-time interactive data center floor map provides color coded bird’s eye view of key data including active power, current & capacity, temperature, humidity, air flow, differential pressure and events on per cabinet basis
- Pinpoint the source for threshold alerts and events as well as rack PDU performance
Power Management
- Complete Data Center Power Monitoring
- Total Usage vs budgeted capacity at a cabinet level
- Monitor cabinet level power usage trends over time
- With outlet level metered iPDUs see aggregated power consumption across multiple power supplies in server
Concept Approach
For every engagement we begin with defining and understanding the project requirements for the data center and identifying the business objectives. This is followed by an assessment and audit of the available assets and inevitable detriments. We then establish the design criteria and create a preliminary design to summarize the associated project build costs.
Concepts maintains relationships with the industries, ‘best-of-breed’, critical infrastructure suppliers, local architect/engineers and construction partners. This ensures you receive the best possible equipment cost, with the most favorable delivery terms and have it installed by the most skilled craftsman. Concept has skillful resources required to operate and manage the BMS system which integrate with IT facility and other systems such as cooling, power, security, lighting, fire suppression and monitoring.
- Physical Site Security
- Lighting Control
- Effective & Efficient Cooling
- Power Distribution
- Alerts indicating conditions that threaten security, safety or uptime
- Remote monitoring capability
- Data collection
- Maintenance scheduling
- Enable planning and upgrades
- Improve efficiency
What are the Benefits of Data Center monitoring?
- Optimized Infrastructure with Data Center Monitoring
Data center monitoring provides real-time data to accurately depict the current power and cooling use, allowing data center management to do a better job of optimizing their infrastructure. - Data center monitoring also helps to improve energy efficiency by more accurate measurement of power consumption and environmental conditions.
- Data Center Monitoring Improves Availability
Data center monitoring can provide a single view of alerts and real-time data for IT management. Centralized event logging allows management to make timely, critical decisions in response to potential disruptions. - Data Center Monitoring in Capacity Planning
Data center monitoring provides real-time data that can help optimize infrastructure resources to match business demands. The value of capacity management revolves around a resource utilization argument. Over-provisioning costs the organization in underutilized or unused resources. Under-provisioning results in failures to meet SLAs, disruptions in service (downtime), the added cost of using co-location or hosting facilities or “rush” charges in provisioning new resources (or building a new data center
Hyper Converged Server Solutions
Hyperconverged infrastructure (HCI) solutions offer businesses the ability to virtualize storage, servers, and their connecting networks. Unlike converged infrastructure, hyperconverged infrastructure leans into software definition as opposed to hardware definition, enabling higher overall flexibility and better expense management over infrastructure use.
Hyper Converged Server Solutions
Hyperconverged infrastructure (HCI) solutions offer businesses the ability to virtualize storage, servers, and their connecting networks. Unlike converged infrastructure, hyperconverged infrastructure leans into software definition as opposed to hardware definition, enabling higher overall flexibility and better expense management over infrastructure use.
With HCI, businesses have greater capability to scale according to usage needs, and resources can be allotted more efficiently between virtualized functions. Hyperconverged infrastructure facilitates more efficient databases, virtual computing like VDI, storage management, and more. Administration of HCI usually resides with data center teams, e.g., server admins or data center admins.
Note that in HCI, the market is beginning to see some solution providers move away from HCI software that is dependent on appliances (integrated/preconfigured software and hardware). Some HCI solutions can be purchased independently of the vendor’s own or dedicated hardware, leaving purchasers with the ability to deploy those solutions on the hardware of their choice.
To qualify for inclusion in the Hyperconverged Infrastructure category, a product must:
Virtualize storage, servers, and their connecting networks
Scale virtualized infrastructure to meet operating requirements
Offer backup or recovery options for virtualized data
Integrate with other infrastructure hardware and software

Hyper Converged Server Solutions

Virtualization, Storage and Backup Solution
Virtualization, Storage and Backup Solution
If you are familiar with virtual environments and products, you may also be heard of many types of virtualizations . Storage virtualization is a significant one of them. Storage virtualization is the pooling of physical storage from multiple storage devices into a seemingly single storage device that is managed by a central console. It is commonly used for virtual machines (VMs) in virtual environments.
Virtualization, Storage and Backup Solution
Compares to traditional storage technologies, storage virtualization has the following advantages:
- Higher disk utilization: While disk utilization with traditional storage technologies is typically only 30%-70%, disk utilization with storage virtualization can reach 70%-90%.
- Greater flexibility: Storage virtualization can accommodate different vendors and different classes of heterogeneous storage platforms, providing greater flexibility in storage resource management.
- Simpler IT environments: storage virtualization reduces the amount of hardware needed to run applications, which simplifies the complexities in the datacenter.
- Easier management: Storage virtualization provides users a centralized way to manage large-capacity storage systems, which can effectively avoid the hassles caused by expansion of storage devices.
- Higher performance: virtualized storage system allocates the bandwidth required for each data access to more storage modules, increasing the overall system access speed.
- Less costly: Storage virtualization requires fewer resources (hardware, physical storage, IT support, etc) than the complex infrastructure and network of traditional datacenter, which reduces up-front investment and post-maintenance costs.
- Modernization adaptable: Transitioning to storage virtualization opens up new opportunities for organizations to take advantage of the latest developments in virtualization, software-defined technologies and hyperconvergence.
These distinct advantages are the reason why many enterprises need storage virtualization.
IT Asset Management & IT Service Management
Too often, assets get tracked in a ton of different places, by a ton of different people. No single person owns things, and no single tool collects and centralizes the information. Naturally, chaos and inaccuracy follow. It’s difficult to make informed decisions. There are even companies where people are being employed just to keep track of IT assets. Systems should do this work.
IT Asset Management & IT Service Management
Providing a single source of truth
Too often, assets get tracked in a ton of different places, by a ton of different people. No single person owns things, and no single tool collects and centralizes the information. Naturally, chaos and inaccuracy follow. It’s difficult to make informed decisions. There are even companies where people are being employed just to keep track of IT assets. Systems should do this work. Without having to relegate time and brain matter to tracking artifacts, monitoring usage, and understanding dependencies, IT employees can focus more on what matters most to the organization. Asset management brings order, and offers a single source of truth for IT teams, management, and ultimately, entire organizations.
Improving utilization and eliminating waste
Asset management keeps information updated, so teams eliminate waste and improve utilization. It saves money by helping avoid unnecessary purchases and cutting licensing and support costs. Increased control also enforces compliance with security and legal policies and reduces risks. The positive implications on costs and productivity benefit the entire organization.

IT Asset Management & IT Service Management

BMR Backup and Recovery
BMR Backup and Recovery
Fast, easy, and reliable data backup and recovery services for a wide variety of enterprise infrastructures, ensuring robust, scalable, and vigorously maintained data safeguards. We develop innovative multi-cloud data protection solutions to protect your data on a wideset & diverse workload ecosystem. VMware integrations to ensure flexible and consistent data protection across the VM container and other application environments.
BMR Backup and Recovery
Our backup & disaster recovery specialists eliminate the malware, delete criminally encrypted files, and quickly restore a clean copy of your valuable data quickly and reliably.
Centralized Management
Our solutions offer enhanced central management built with role-based access control (RBAC) modules for administrators to define specific roles within your organization.
Cloud Storage
We create solutions that allow you to store unlimited amounts of data in the cloud and extend retention by transferring multiple data revisions into separate off-site vaulting.
Data Replication
Our solutions protect you from disastrous data loss using the cloud to store your data off-site and replicate your data with a remote physical or virtual backup appliance.
Cyber Security - Ransom Defense for Server and End Point Security
Endpoints pose significant security risks. Savvy attackers can exploit endpoint vulnerabilities to steal confidential information or disrupt IT services, resulting in revenue loss and costly regulatory fines and legal settlements. By taking a defense-in-depth approach to ransomware —instituting a wide range of endpoint security controls—you can strengthen your security posture and reduce exposure.
Cyber Security - Ransom Defense for Server and End Point Security
EDR tools let you proactively identify and investigate suspicious activity on endpoints.
Originated as an additional security layer back in 2013, EDR solutions continuously
monitor, record and analyze endpoint activities, helping IT and security professionals
efficiently uncover and mitigate advanced threats.
Many EDR solutions use advanced analytics, analyzing endpoint events to detect
malicious activities that might otherwise go unnoticed. EDR tools provide visibility
into suspicious endpoint behavior in real time, helping you to stop threats before
they take root and spread across the business.
Extended Detection & Response (XDR)
To uncover more threats and provide more context to their analyses, tools are
evolving to include networks, clouds, and endpoints with more advanced analytics
and automation
Privileged management is a critical, and often overlooked, component of an effective
endpoint security strategy. Malicious insiders or external attackers exploit endpoint
administrator accounts to gain a foothold in a network, and then move laterally to
penetrate or disrupt higher-value targets.
Privileged management solutions restrict privileged access and enforce application
control, granting users the minimum set of rights required to perform their jobs,
strengthening security, without impairing user productivity. This mitigates threats
at the endpoint of entry, and prevents lateral movement and the spread of malware,
ultimately helping you reduce exposure and prevent the encryption of ransomware.

Cyber Security - Ransom Defense for Server and End Point Security

Cyber Security - Next Generation Firewall / UTM Appliance
Cyber Security - Next Generation Firewall / UTM Appliance
Network security now is the most important thing to have for all businesses, no matter it’s a small SMB or a complicated enterprise. While researching network security solutions, companies are coped with various options from a solutions point of view for dealing with every threat to the solutions which merge services into a single appliance.
Cyber Security - Next Generation Firewall / UTM Appliance
The firewall market throughout the last five years had been dwelt by two fundamental ideas of solutions, which in some situations create confusion about the difference, scope, and functionality. To understand the basic theme behind these terms, their differences and to choose best for your company keep on reading the article.
Unified Threat Management (UTM)
The idea to launch the UTM firewall grew naturally with time, according to the demands of the businesses and the development of the security industry itself. As novel threats and vulnerabilities were found, the firewall was raised with the latest features and capabilities. For this purpose, a UTM system was launched as a system that includes network hardware devices, cloud services, or virtual devices that save businesses from security hazards in a modified way by joining and incorporating different security services and lineaments. UTM devices are mostly boxed as network protection devices, which can aid in protecting networks against compounded security risks, including the attacks and malware that instantly point divided portions of a network.
UTM virtual network appliances and cloud services are gaining popularity because of the network security they provide, specifically for small and medium-sized enterprises. They both work the demands of a business as on-premises network protection appliances by presenting ease of use and centralized control for establishing network security defense.
As UTM systems and NGFWs are most of the time comparable, UTM appliances contain security lineaments that are not offered by the NGFWs. Primitively evolved to meet the network security cracks led by traditional firewalls, NGFWs generally include intrusion prevention systems and application intelligence, and denial-of-service security. UTM appliances provide several layers of network protection, including antivirus, next-generation firewalls, prevention systems/intrusion detection, spam filtering, virtual private networks (VPN), and URL filtering for website content.
As a restriction to the UTM firewall, we can highlight matters related to execution, as all security operations are centralized in one product. The matter becomes more visible in business environments, with a rich volume of packets and deficient hardware, leading to the impairments of the execution of security rules implemented in the environment. Then again, centralization can be unbelievably positive for businesses where an individual device will fulfill most of the security requirements, with significant competitive values in comparison to buying individual products to match the requirements individually. Unified threat management is an adjacent platform for security appliances, especially suitable for SMBs.
Casual feature sets devolve into three primary subsets: virtual private network/intrusion prevention system (IPS)/ firewall, messaging security, and safe web gateway security plus web antivirus.
Next-Generation Firewall
The NGFW was formulated with the need to solve the operational inadequacy announced by the UTMs. It showcases application control features and cryptic packet inspection in a remarkably cohesive and performing architecture. Complementary lineaments like malware and virus protection, web proxy, and others exist in the UTM firewall are not a component of the NGFW architecture as these lineaments have been outsourced and removed, assuring rich scalability grades for huge environments.
The basic share of NGFW rests in the technological improvements built from the cryptic packet inspection and the presence of applications, irrespective of the ports and protocols. Unitedly, these lineaments not only permit threats to be precluded, but they can also make more efficient and dynamic availability control policies for new eras security hazards. NGFWs are deep-packaged inspection firewalls that go outside the protocol/port inspection and closures to provide an application-level review, contributing intelligence, and intrusion bar from out of the firewall.
A Next-generation firewall should not be mixed up with an intrusion prevention system, which contains a non-enterprise firewall or a commodity, or an IPS and a firewall in the same devices that are not tightly incorporated.
Cyber Security – Exclusive Email Security
Email security is essential for businesses and individuals to protect sensitive information and prevent catastrophic data breaches. Here are some benefits of email security. Detect and resolve email threats such as phishing or spoofing, which can lead to devastating breaches and the risk of malware or other harmful computer viruses.
Cyber Security – Exclusive Email Security
- Protects against phishing and spoofing attacks: Email security can help detect and resolve email threats such as phishing or spoofing, which can lead to devastating breaches and the risk of malware or other harmful computer viruses.
- Prevents data breaches: Email encryption can prevent accidents and aid in the prevention of costly data breaches. It protects confidential information such as credit card numbers, bank accounts, employee PII, and intellectual property.
- Improves confidentiality: Secure email encryption solutions can bolster confidentiality by ensuring that only the intended recipients can access the email content.
- Identifies malicious and spam emails: Email security can help detect malicious or spam emails that might breach the mail system’s spam filter, making accounts vulnerable to engaging with such emails.
- Avoids business risks and remains compliant: Email encryption services can help businesses avoid risks and remain compliant with industry regulations.
- Safeguards sensitive information: Email security can protect sensitive information, such as intellectual property, financial records, and top-secret company information and trade secrets, from interception by malicious actors like hackers and cybercriminals.
- Real-time protection: Email security solutions can provide real-time protection against zero-day exploits by providing anti-malware and anti-spam protection.
- Avoids compromised accounts and identity theft: Email encryption can help avoid compromised accounts and identity theft by preventing attackers from stealing login credentials and other personal data or installing malware.

Cyber Security – Exclusive Email Security
IoT, SCADA & Simulation Solution
IoT, SCADA & Simulation Solution
SCADA software system is a device monitoring and controlling framework. The supervisory control includes, taking action and control through remote locations for various control mechanisms and processes. Various kinds of data can be acquired from network of devious (connected through wireless/wired communication systems) for storage, processing and analytics to aid decision making.
IoT, SCADA & Simulation Solution
Features Supported by SCADA:
System Management Features:
The interactive user interface of the SCADA system has evolved over a period of time.It includes graphical representation of the whole system, showing data in a consolidated manner.
Typically a SCADA solution will support following two types of system management features:
- Device Management: The number of nodes or devices being monitored or maintained is visible from the UI and can be subcategorized further into different parameters.
For instance, in case of industrial automation, the control units installed in a particular production floor can be categorized under geographical location and admin level of that particular system.
Also an overview of the whole production floor can be seen, with the total number of such control units installed. The number of devices installed, depend on the type of network topology used.
- User Management: The permission and roles can be defined under user management panel with respect to the level of users. The specific admin roles can be assigned and limited access to other level of user for various data and for the interface as well, can be imposed.
IP-Telephony & VoIP Solution
IP telephony encompasses the technologies, products, and services that enable voice calling, voicemail, video calling, video conferencing, faxing, messaging, and other telephony-related services using IP’s packet-switched connections. Such information traditionally travels over the dedicated circuit-switched connections of the public switched telephone network (PSTN).
IP-Telephony & VoIP Solution
IP telephony encompasses the technologies, products and services that enable voice calling, voicemail, video calling, video conferencing, faxing, messaging and other telephony-related services using IP’s packet-switched connections. Such information traditionally travels over the dedicated circuit-switched connections of the public switched telephone network (PSTN), also known as the plain old telephone service. Instead, IP telephony technology converts calls, faxes and text messages into packets of data that travel across computer network lines, avoiding the tolls of PSTN.
Voice over Internet Protocol, or VoIP, is the set of standardized technologies that delivers voice calls via the internet or a private IP-based network. In the narrowest understanding of the term, VoIP is voice over IP only — a subset of IP telephony that does not include other, non-voice-based communication services, such as faxing or text messaging. But, again, it’s generally fine to use the terms VoIP and IP telephony synonymously, as, indeed, many do.

IP-Telephony & VoIP Solution

Enterprise Switching and Router Solution
Enterprise Switching and Router Solution
Your network infrastructure enables everyone in your company to connect to each other, to customers, to business partners, to important applications and to the Internet. The way a network operates is to connect computers and peripherals using two pieces of equipment – switches and routers. These two let the devices connected to your network talk with each other as well as talk to other networks.
Enterprise Switching and Router Solution
Switching and Routing
Switches are used to connect multiple devices on the same network within a building or campus. The switch serves as a controller, allowing the various devices to share information and talk to each other. Through information sharing and resource allocation, switches save you money and increase productivity.
Routers are used to tie multiple networks together. They connect your business to the outside world, protect your information from security threats, and even decide which computers get priority over others. Routers analyze the data being sent over your network, change how it is packaged and send it to another network or over a different type of network.
Campus WIFI and Physical Networking Solution
Today’s smart campus network is built on a foundation of connectivity designed to increase productivity, efficiency, learning, and safety. Reliable high-speed fiber rings, inside plant fiber, PoE (power over Ethernet) and powered fiber create a solid infrastructure for Wi-Fi.
Campus WIFI and Physical Networking Solution
Universal connectivity
Universal connectivity is the primary requirement for a smart campus, supporting all manner of users, devices and applications. It includes a campus-wide network featuring copper and fiber backbone; ubiquitous wireless coverage—Wi-Fi and cellular, indoors and out; high-speed switching and reliable powered fiber; plus, the vision and experience to bring it all together.
Connected edge devices
Every campus is different, but all face a common challenge: how to power and connect a variety of remote devices to ensure network dependability and physical safety throughout the campus. CommScope’s smart campus solutions make it possible without intruding on the environment.

Campus WIFI and Physical Networking Solution

ILL and P2P / P2MP Connectivity Solution
ILL and P2P / P2MP Connectivity Solution
When weighing your options, point-to-point vs. point-to-multipoint are viable options for your business needs. Both solutions deliver a symmetrical, private fiber connection, enabling businesses to seamlessly communicate across geographically diverse locations as if each were on the same local area network (LAN). When comparing point-to-point vs. point-to-multipoint, simply evaluate the number of endpoints your business needs to connect.
ILL and P2P / P2MP Connectivity Solution
Point-to-Point (P2P) Connection
For many one- and two-location enterprise businesses, a point-to-point broadband connection is ideal. This circuit is a private, reliable, high-speed fiber connection that links two endpoints of your choosing. These endpoints can include business locations and data centers or co-locations and IT vendors. This Ethernet connection is easy to implement and an affordable network solution.
Point-to-MultiPoint (P2MP) Connection
For businesses with two or more locations, a point-to-multipoint broadband solution allows three or more separate points to work — seemingly effortlessly — as one cohesive network. This solution replaces the need for VPN management and enables your sites to communicate with one another, a data center or colocation facility, or any other business-critical location.
RFID Solution
RFID Solutions believes that its success is built upon the success of its customers and works directly with them to produce cost effective RFID solutions that are on time and under budget. RFID Solutions provides both hardware and software and is certified using the latest RFID devices and technologies available. RFID Solutions works with businesses in the private sector as well as civil and government agencies.
RFID Solution
RFID Solutions works with businesses in the private sector as well as civil and government agencies.
The company produces a wide variety of enterprise-level RFID systems including:
- Asset Tracking and Inventory Control
- Manufacturing and Work in Progress (WIP)
- Supply Chain, Warehouse Logistics and Distribution Centers
- Retail Business Intelligence
- Parking Lot and Gate Access
- File Tracking, Legal and Medical records management
- Criminal Evidence and Chain of Custody
- Cattle Tracking
- RFID Integration
- Custom RFID Solutions

RFID Solution

Video Conferencing Solutions
Video Conferencing Solutions
As organizations embrace the hybrid working style which provides flexibility to work in the office or at home, enabling proper video meetings for remote and in-person employees will ensure efficient communication and boost engagement. Video conference solutions which include conference cameras, smart video bar, smart projector, and interactive display whether it’s for a small huddle room, large meeting room or even home office setting to strengthen your virtual meetings and remote communications.
Video Conferencing Solutions
Start video conferencing with one click
Get right into your online meetings with the all-in-one smart video conference bar which hooks up to your device, whether it’s a TV, monitor, projector or interactive display. With built-in Android system and a video conference app, the VC01A Smart Video Bar is designed to enable PC-less video conferencing and screen sharing from personal devices.
Cloud and On-Prem Business Email Collaboration Solution
Cloud business solutions have changed the way we conduct business dramatically and how employees accomplish day-to-day tasks. The zero upfront costs and extensive scalability of cloud environments are enabling business leaders to explore innovative ideas, reduce time-to-market, and expand to new frontiers. At the same time, the accessibility and global reach of cloud solutions are enabling users to work wherever they want, whenever they want.
Cloud and On-Prem Business Email Collaboration Solution
Benefits of Cloud Business Solutions?
There are so many advantages of cloud business solutions. Look at the chart below to learn about them and why your move to the cloud may be just what your business needs.
| Benefit | Description |
| Speed and flexibility | Cloud business solutions eliminate many time-consuming IT processes. Software as a Service (SaaS) business solutions, for example, don’t require physical hardware or even any software installation and maintenance. This can help startups hit the ground running, while already-operational businesses can speed up time-to-market and focus on core business processes. |
| Reduced IT infrastructure costs | With cloud solutions (except for on-premises private clouds), you don’t need to invest in physical IT infrastructure. By removing expensive upfront costs, businesses can enjoy a healthier cash flow. The CAPEX savings can be used to fund projects in marketing, sales, research, and operations. |
| Scalability | Compared to traditional on-premises business solutions, cloud business solutions are infinitely more scalable. This scalability, which is accompanied by flexible pricing (e.g., most SaaS business solutions allow a monthly subscription model on a per-user-per-month pricing basis), allows you to start as small as you want and grow as the need arises. It even allows you to expand and contract spending, which is perfect for seasonal demands. |
| Business continuity | Cloud business solutions are backed by robust infrastructure, comprising multiple datacenters in different geographical regions. Thus, even if a disaster strikes in one region, your business applications can still be accessible. You can’t enjoy that level of business continuity if you rely on business solutions that run on your own datacenter. If that datacenter becomes incapacitated, you can suffer considerable downtime. |
| Security | When you use a cloud business solution, your data isn’t stored on your users’ devices by default. This alone reduces risk. Even if a user’s device is stolen, your data will still be safe in the cloud. Furthermore, particularly in the case of SaaS business solutions, software patches—arguably the most effective defense against known threats—are done regularly and automatically by the solutions provider. This ensures users are delivered the safest version of the solution at all times. |
| Collaboration | SaaS solutions like Google Docs, Office 365, Trello, Asana, Jira, HubSpot and many others allow multiple users to work on the same platform, or even the same document, simultaneously. This enables users to perform collaborative work even if they’re not in the same room or country. |
| Storage options | Many cloud solutions have virtually unlimited capacity. As long as you can afford the corresponding subscription cost, you can provide your users with all the storage they need to get their work done. Conversely, you can also reduce storage capacity once your need goes down. This storage flexibility is unheard of in traditional business solutions, where you need to forecast maximum storage requirements (even if it isn’t filled up most of the time) and purchase that capacity in advance. |
| Mobility and easy access | Cloud-based business solutions make it possible for users to work even when they’re on the go. In the case of cloud-based VDI desktops, it’s even possible for users to access full-featured Windows applications from anywhere on any endpoint device. |

Cloud and On-Prem Business Email Collaboration Solution
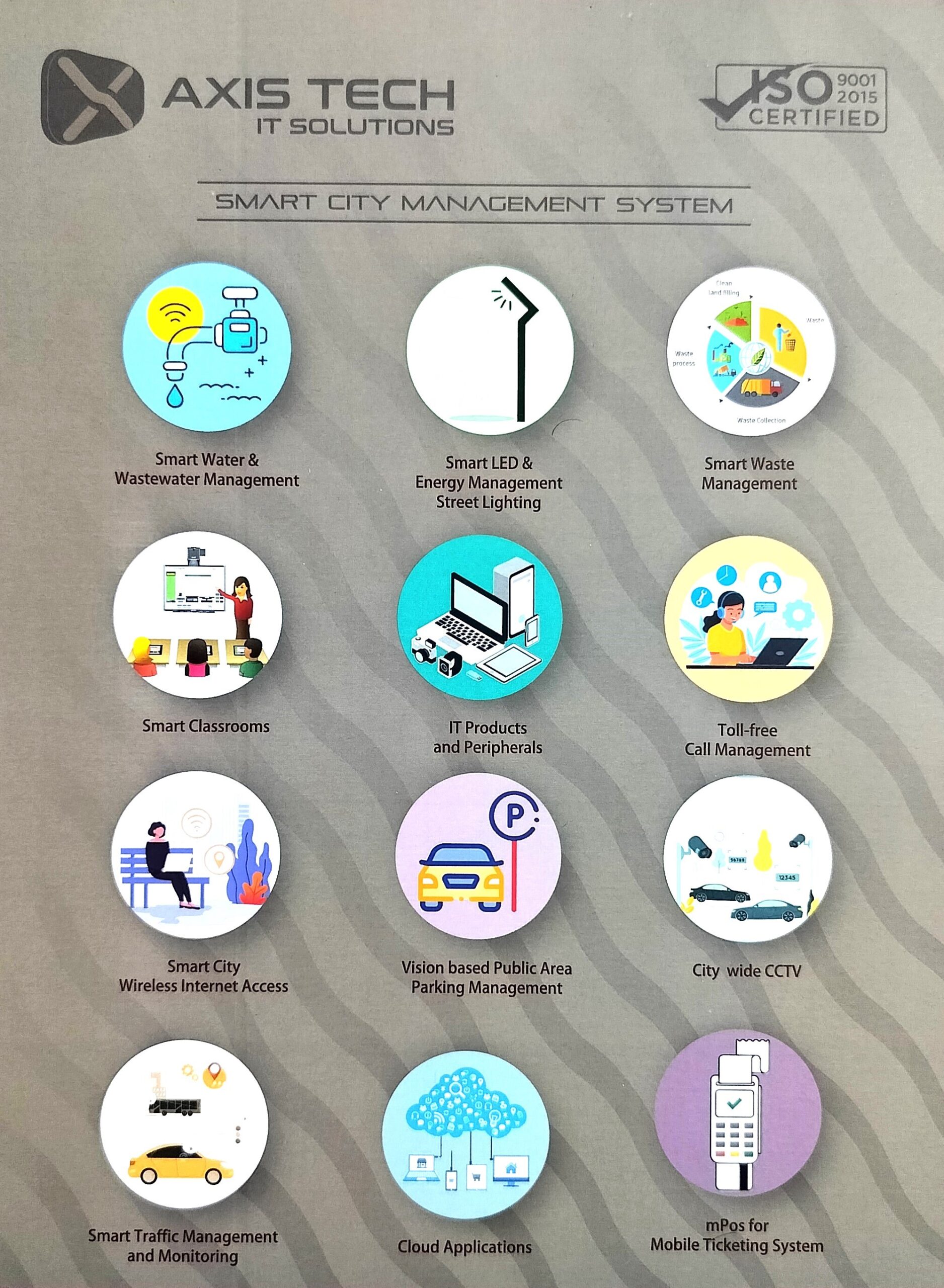
Our Smart City Management System